3D Secure: The Backbone of Online Payment Security
3D Secure: The Backbone of Online Payment Security
Author: Abdullah Almanie
Author: Abdullah Almanie
Oct 13, 2024
In the age of digital commerce, where tapping a screen can instantly purchase anything from groceries to vacations, the security of our online transactions is paramount. At the heart of millions of online purchases lies a security measure known as 3D Secure. This technology plays a crucial role in protecting against fraud while striving to maintain a smooth user experience.
3D Secure, short for “Three Domain Secure,” is a protocol designed to add an extra layer of security to online transactions. It’s the reason why you’re sometimes redirected to a separate page to provide additional verification when making an online purchase. While it may seem like an extra step, this system represents the frontline defence in the ongoing battle against e-commerce fraud.
How does this protocol balance robust security with user experience? What makes it so effective in combating online fraud? And why has it become an integral part of e-commerce worldwide?
The History
As e-commerce boomed in the late 1990s, so did the challenges of online payment security. Card-not-present (CNP) fraud began to surge, creating a pressing need for a robust authentication system.
In 1999, Visa recognized this need and began developing a solution. Their efforts culminated in the launch of 3D Secure 1.0 in 2001, branded as “Verified by Visa.” This technology added an extra layer of security to online transactions by requiring cardholders to authenticate themselves with their card issuer during checkout.
The impact of Visa’s innovation was swift and far-reaching. Other major card networks quickly followed suit:
Mastercard introduced “SecureCode”
JCB rolled out “J/Secure”
American Express launched “SafeKey”
While each network branded their service differently, all were based on the core 3D Secure protocol, creating a unified approach to online payment security.
The Three Domains
The “3D” in 3D Secure refers to the three key domains involved in the secure transaction process. Understanding these domains is crucial to grasping how 3D Secure functions as a comprehensive security protocol.
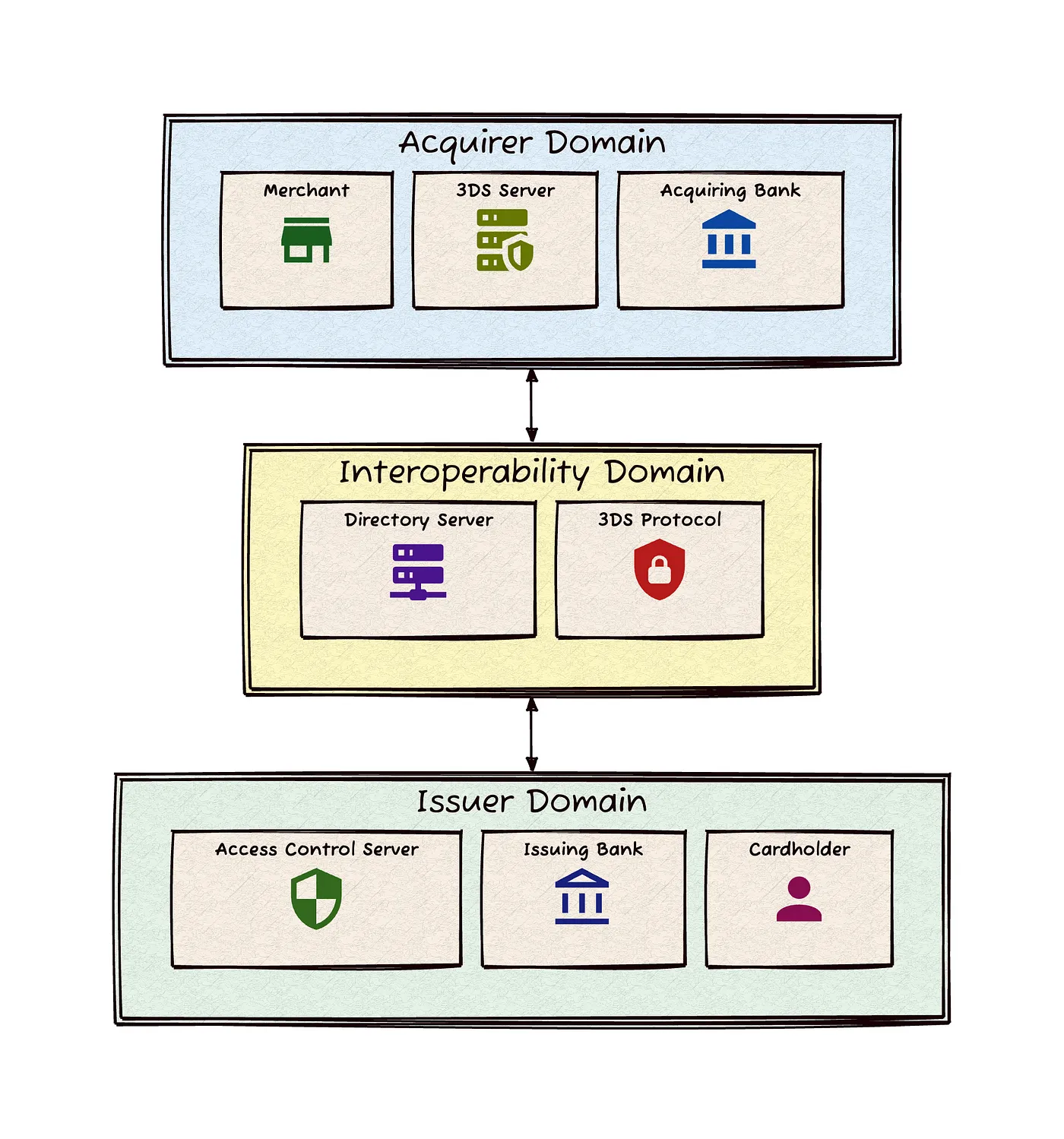
1. Acquirer Domain
The Acquirer Domain represents the merchant and the bank or financial institution that processes payments on behalf of the merchant (known as the acquiring bank).
Role in 3D Secure:
Initiates the 3D Secure process during checkout
Sends transaction details to the Issuer Domain
Receives authentication results and proceeds with the transaction accordingly
2. Issuer Domain
The Issuer Domain represents the cardholder and the bank or financial institution that issued the payment card (known as the issuing bank).
Role in 3D Secure:
Verifies the cardholder’s identity
Assesses the risk of the transaction
Sends authentication results back to the other domains
3. Interoperability Domain
The Interoperability Domain acts as a bridge between the Acquirer and Issuer Domains, facilitating secure communication and data exchange.
Role in 3D Secure:
Routes messages between the Acquirer and Issuer Domains
Ensures all parties are using compatible versions of the 3D Secure protocol
Maintains the integrity and security of data exchanged between domains
The 3D Secure Flow
The 3D Secure process involves a complex choreography of interactions between the cardholder, merchant, issuing bank, and various intermediary systems. Let’s break down this flow into steps for a comprehensive understanding.
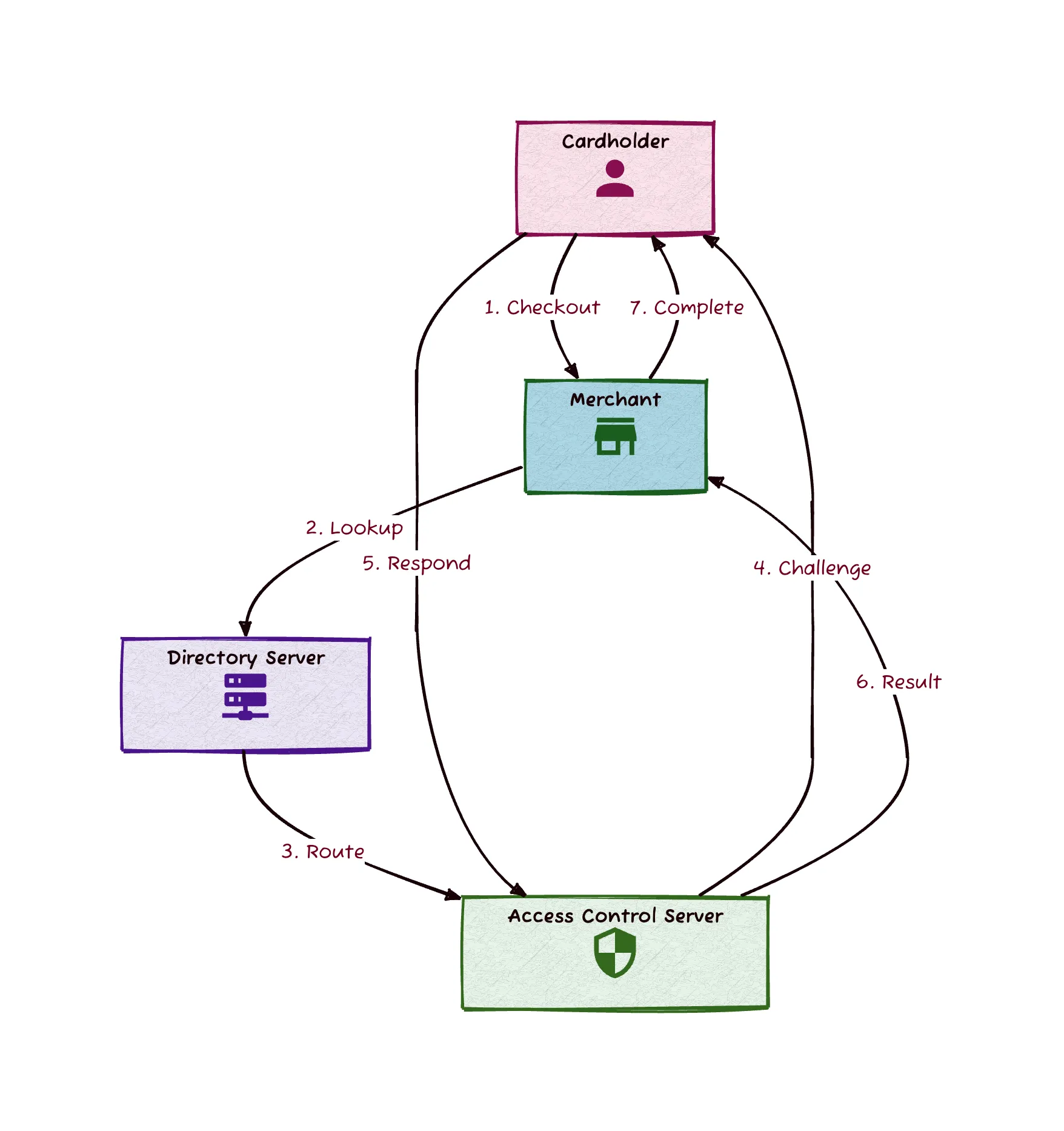
1. Transaction Initiation
The cardholder begins the checkout process on the merchant’s website or app.
The cardholder enters their payment card details.
2. Directory Server (DS) Lookup
The merchant’s 3D Secure server (part of the Acquirer Domain) sends a lookup request to the Directory Server (DS) in the Interoperability Domain.
This request checks if the card is enrolled in 3D Secure.
3. Issuer ACS Routing
If the card is enrolled, the DS routes the request to the appropriate Access Control Server (ACS) in the Issuer Domain.
The ACS is operated by the card issuer or a third-party provider on their behalf.
4. Risk-Based Authentication (RBA)
The ACS performs a risk assessment of the transaction.
Factors considered may include transaction amount, merchant type, cardholder’s transaction history, device information, and more.
Based on the risk assessment, the ACS decides whether to:
a) Proceed with frictionless authentication (if the risk is deemed low)
b) Require challenge-based authentication (if additional verification is needed)
5a. Frictionless Flow
If frictionless authentication is chosen:
The ACS generates an authentication response without cardholder interaction.
This response is sent back through the DS to the merchant’s 3D Secure system.
5b. Challenge Flow
If challenge-based authentication is required:
The ACS initiates a challenge request.
The challenge interface is displayed to the cardholder, typically via redirect.
The cardholder is asked to provide additional verification. In Saudi Arabia, this often involves entering an OTP sent via SMS.
6. Authentication Result Generation
The ACS verifies the provided authentication (in challenge flow) or completes the frictionless authentication.
It generates an authentication result, which includes:
A unique transaction ID
The authentication status (successful, failed, or unable to authenticate)
A cryptographic signature (authentication value cryptogram) to ensure the integrity of the result
Electronic Commerce Indicator (ECI) indicating the outcome of a 3DS authentication
7. Result Transmission
The authentication result is sent from the ACS back through the Directory Server.
The DS forwards this result to the merchant’s 3D Secure server.
8. Merchant Verification
Merchant’s system checks for the completion of the authentication process.
Verifies the presence of an ECI value indicating successful authentication and liability shift.
9. Transaction Completion
If authentication was successful, the merchant proceeds with the transaction.
If authentication failed or couldn’t be completed, the merchant typically declines the transaction.
This entire process, while complex, typically occurs within a matter of seconds, providing a balance between robust security and a smooth user experience. The flow can adapt based on the specific implementation, risk levels, and regulatory requirements in different regions or for different card issuers.
The Liability Shift: A Win for Merchants
One of the most significant advantages of 3D Secure for merchants is the liability shift. This feature fundamentally changes who bears the financial responsibility in cases of fraudulent transactions, providing a substantial benefit to merchants who implement 3D Secure.
Without 3D Secure:
Merchants were typically liable for fraudulent card-not-present (CNP) transactions
This resulted in significant financial risks for online businesses
With 3D Secure:
Liability shifts from the merchant to the card issuer for authenticated transactions
This applies even if the transaction is later discovered to be fraudulent
What does this mean for merchants?
Successful 3DS Authentication:
If a transaction is authenticated via 3D Secure and later turns out to be fraudulent, the issuing bank bears the cost
The merchant is protected from fraud-related chargeback liability, but remains liable for disputes related to goods/services
Failed or Bypassed Authentication:
If the issuer declines to authenticate or authentication fails, the merchant can choose to proceed with the transaction
In this case, the liability remains with the merchant
Benefits for Merchants
1. Reduced Financial Risk:
Protection against fraudulent transaction losses
Fewer chargebacks to manage
2. Increased Confidence:
Ability to accept higher-risk transactions with less concern
Potential for expanded customer base and higher sales
3. Cost Savings:
Reduced need for additional fraud prevention measures
Lower operational costs associated with managing fraud and chargebacks
4. Improved Cash Flow:
Fewer funds held in reserve to cover potential chargebacks.
3D Secure 2.0
As e-commerce continued to evolve, so did the need for more sophisticated and user-friendly security measures. This led to the development of 3D Secure 2.0, a significant upgrade to the original protocol.
Key Improvements in 3DS 2.0
1. Enhanced User Experience:
Eliminated clunky pop-up windows
Enabled in-app authentication for mobile devices
2. Frictionless Authentication:
Introduced risk-based authentication
Allows low-risk transactions to proceed without additional cardholder interaction
3. Richer Data Exchange:
Supports over 100 data elements (compared to 15 in 3DS 1.0)
Enables a more accurate risk assessment
4. Mobile-First Approach:
Optimized for mobile transactions
Supports biometric authentication methods (fingerprint, facial recognition)
Regulatory Landscape
The implementation of 3D Secure is often driven by regulatory requirements aimed at enhancing payment security. While regulations vary across regions, let’s focus on the landscape in Saudi Arabia, with a brief comparison to other significant regulatory frameworks.
Saudi Arabia: SAMA’s Mandate
The Saudi Central Bank (SAMA) has taken a proactive approach to securing digital payments:
Mandatory 3D Secure:
SAMA has mandated the use of 3D Secure for all online card transactions in the Kingdom
This requirement applies to both domestic and international transactions
OTP Authentication:
One-Time Passwords (OTPs) sent via SMS are the primary method of authentication
This aligns with the strong customer authentication (SCA) principle
Comparison with Other Regions
Europe: PSD2 and SCA
The Second Payment Services Directive (PSD2) mandates Strong Customer Authentication (SCA) for electronic payments
3D Secure 2.0 is widely used to meet SCA requirements
Unlike Saudi Arabia, Europe allows for various authentication methods beyond OTP
United States
No federal mandate for 3D Secure
Implementation is driven by card networks and individual financial institutions
Impact on 3D Secure Implementation
1. Standardization:
SAMA’s mandate ensures a consistent approach across all online transactions in Saudi Arabia
This standardization can lead to higher user familiarity and acceptance
2. Authentication Methods:
The focus on OTP in Saudi Arabia may limit the adoption of newer authentication methods like biometrics
However, it ensures a uniform experience for users across different banks and merchants
3. Merchant Considerations:
Merchants operating in Saudi Arabia must ensure their payment systems are fully compliant with SAMA’s 3D Secure requirements
This may require specific customizations for the Saudi market
4. International Transactions:
Saudi cards used internationally and international cards used in Saudi Arabia must still go through the 3D Secure process
This can sometimes lead to friction, especially if users are unfamiliar with the Saudi-specific implementation
SAMA’s strong stance on 3D Secure reflects the Kingdom’s commitment to securing digital payments and aligns with global trends towards enhanced online transaction security. While the specific implementation may differ from other regions, the core goal of reducing fraud and protecting consumers remains consistent.
Conclusion
3D Secure has become an indispensable component of the global e-commerce ecosystem. From its inception as a Visa innovation to its current status as a regulatory requirement in many regions, including Saudi Arabia, this technology has consistently evolved to meet the changing landscape of online fraud. The balance it strikes between robust security and user experience, coupled with the significant advantage of liability shift for merchants, has cemented its place in digital transactions worldwide.
As we look to the future, the continued evolution of 3D Secure, particularly with version 2.0, promises even greater security with reduced friction. While implementation may vary across different regions, the core principle remains the same: protecting consumers and merchants in an increasingly digital marketplace. As e-commerce continues to grow and new payment technologies emerge, 3D Secure is likely to remain at the forefront of online payment security, adapting and improving to meet new challenges in the ever-changing world of digital commerce.
In the age of digital commerce, where tapping a screen can instantly purchase anything from groceries to vacations, the security of our online transactions is paramount. At the heart of millions of online purchases lies a security measure known as 3D Secure. This technology plays a crucial role in protecting against fraud while striving to maintain a smooth user experience.
3D Secure, short for “Three Domain Secure,” is a protocol designed to add an extra layer of security to online transactions. It’s the reason why you’re sometimes redirected to a separate page to provide additional verification when making an online purchase. While it may seem like an extra step, this system represents the frontline defence in the ongoing battle against e-commerce fraud.
How does this protocol balance robust security with user experience? What makes it so effective in combating online fraud? And why has it become an integral part of e-commerce worldwide?
The History
As e-commerce boomed in the late 1990s, so did the challenges of online payment security. Card-not-present (CNP) fraud began to surge, creating a pressing need for a robust authentication system.
In 1999, Visa recognized this need and began developing a solution. Their efforts culminated in the launch of 3D Secure 1.0 in 2001, branded as “Verified by Visa.” This technology added an extra layer of security to online transactions by requiring cardholders to authenticate themselves with their card issuer during checkout.
The impact of Visa’s innovation was swift and far-reaching. Other major card networks quickly followed suit:
Mastercard introduced “SecureCode”
JCB rolled out “J/Secure”
American Express launched “SafeKey”
While each network branded their service differently, all were based on the core 3D Secure protocol, creating a unified approach to online payment security.
The Three Domains
The “3D” in 3D Secure refers to the three key domains involved in the secure transaction process. Understanding these domains is crucial to grasping how 3D Secure functions as a comprehensive security protocol.

1. Acquirer Domain
The Acquirer Domain represents the merchant and the bank or financial institution that processes payments on behalf of the merchant (known as the acquiring bank).
Role in 3D Secure:
Initiates the 3D Secure process during checkout
Sends transaction details to the Issuer Domain
Receives authentication results and proceeds with the transaction accordingly
2. Issuer Domain
The Issuer Domain represents the cardholder and the bank or financial institution that issued the payment card (known as the issuing bank).
Role in 3D Secure:
Verifies the cardholder’s identity
Assesses the risk of the transaction
Sends authentication results back to the other domains
3. Interoperability Domain
The Interoperability Domain acts as a bridge between the Acquirer and Issuer Domains, facilitating secure communication and data exchange.
Role in 3D Secure:
Routes messages between the Acquirer and Issuer Domains
Ensures all parties are using compatible versions of the 3D Secure protocol
Maintains the integrity and security of data exchanged between domains
The 3D Secure Flow
The 3D Secure process involves a complex choreography of interactions between the cardholder, merchant, issuing bank, and various intermediary systems. Let’s break down this flow into steps for a comprehensive understanding.

1. Transaction Initiation
The cardholder begins the checkout process on the merchant’s website or app.
The cardholder enters their payment card details.
2. Directory Server (DS) Lookup
The merchant’s 3D Secure server (part of the Acquirer Domain) sends a lookup request to the Directory Server (DS) in the Interoperability Domain.
This request checks if the card is enrolled in 3D Secure.
3. Issuer ACS Routing
If the card is enrolled, the DS routes the request to the appropriate Access Control Server (ACS) in the Issuer Domain.
The ACS is operated by the card issuer or a third-party provider on their behalf.
4. Risk-Based Authentication (RBA)
The ACS performs a risk assessment of the transaction.
Factors considered may include transaction amount, merchant type, cardholder’s transaction history, device information, and more.
Based on the risk assessment, the ACS decides whether to:
a) Proceed with frictionless authentication (if the risk is deemed low)
b) Require challenge-based authentication (if additional verification is needed)
5a. Frictionless Flow
If frictionless authentication is chosen:
The ACS generates an authentication response without cardholder interaction.
This response is sent back through the DS to the merchant’s 3D Secure system.
5b. Challenge Flow
If challenge-based authentication is required:
The ACS initiates a challenge request.
The challenge interface is displayed to the cardholder, typically via redirect.
The cardholder is asked to provide additional verification. In Saudi Arabia, this often involves entering an OTP sent via SMS.
6. Authentication Result Generation
The ACS verifies the provided authentication (in challenge flow) or completes the frictionless authentication.
It generates an authentication result, which includes:
A unique transaction ID
The authentication status (successful, failed, or unable to authenticate)
A cryptographic signature (authentication value cryptogram) to ensure the integrity of the result
Electronic Commerce Indicator (ECI) indicating the outcome of a 3DS authentication
7. Result Transmission
The authentication result is sent from the ACS back through the Directory Server.
The DS forwards this result to the merchant’s 3D Secure server.
8. Merchant Verification
Merchant’s system checks for the completion of the authentication process.
Verifies the presence of an ECI value indicating successful authentication and liability shift.
9. Transaction Completion
If authentication was successful, the merchant proceeds with the transaction.
If authentication failed or couldn’t be completed, the merchant typically declines the transaction.
This entire process, while complex, typically occurs within a matter of seconds, providing a balance between robust security and a smooth user experience. The flow can adapt based on the specific implementation, risk levels, and regulatory requirements in different regions or for different card issuers.
The Liability Shift: A Win for Merchants
One of the most significant advantages of 3D Secure for merchants is the liability shift. This feature fundamentally changes who bears the financial responsibility in cases of fraudulent transactions, providing a substantial benefit to merchants who implement 3D Secure.
Without 3D Secure:
Merchants were typically liable for fraudulent card-not-present (CNP) transactions
This resulted in significant financial risks for online businesses
With 3D Secure:
Liability shifts from the merchant to the card issuer for authenticated transactions
This applies even if the transaction is later discovered to be fraudulent
What does this mean for merchants?
Successful 3DS Authentication:
If a transaction is authenticated via 3D Secure and later turns out to be fraudulent, the issuing bank bears the cost
The merchant is protected from fraud-related chargeback liability, but remains liable for disputes related to goods/services
Failed or Bypassed Authentication:
If the issuer declines to authenticate or authentication fails, the merchant can choose to proceed with the transaction
In this case, the liability remains with the merchant
Benefits for Merchants
1. Reduced Financial Risk:
Protection against fraudulent transaction losses
Fewer chargebacks to manage
2. Increased Confidence:
Ability to accept higher-risk transactions with less concern
Potential for expanded customer base and higher sales
3. Cost Savings:
Reduced need for additional fraud prevention measures
Lower operational costs associated with managing fraud and chargebacks
4. Improved Cash Flow:
Fewer funds held in reserve to cover potential chargebacks.
3D Secure 2.0
As e-commerce continued to evolve, so did the need for more sophisticated and user-friendly security measures. This led to the development of 3D Secure 2.0, a significant upgrade to the original protocol.
Key Improvements in 3DS 2.0
1. Enhanced User Experience:
Eliminated clunky pop-up windows
Enabled in-app authentication for mobile devices
2. Frictionless Authentication:
Introduced risk-based authentication
Allows low-risk transactions to proceed without additional cardholder interaction
3. Richer Data Exchange:
Supports over 100 data elements (compared to 15 in 3DS 1.0)
Enables a more accurate risk assessment
4. Mobile-First Approach:
Optimized for mobile transactions
Supports biometric authentication methods (fingerprint, facial recognition)
Regulatory Landscape
The implementation of 3D Secure is often driven by regulatory requirements aimed at enhancing payment security. While regulations vary across regions, let’s focus on the landscape in Saudi Arabia, with a brief comparison to other significant regulatory frameworks.
Saudi Arabia: SAMA’s Mandate
The Saudi Central Bank (SAMA) has taken a proactive approach to securing digital payments:
Mandatory 3D Secure:
SAMA has mandated the use of 3D Secure for all online card transactions in the Kingdom
This requirement applies to both domestic and international transactions
OTP Authentication:
One-Time Passwords (OTPs) sent via SMS are the primary method of authentication
This aligns with the strong customer authentication (SCA) principle
Comparison with Other Regions
Europe: PSD2 and SCA
The Second Payment Services Directive (PSD2) mandates Strong Customer Authentication (SCA) for electronic payments
3D Secure 2.0 is widely used to meet SCA requirements
Unlike Saudi Arabia, Europe allows for various authentication methods beyond OTP
United States
No federal mandate for 3D Secure
Implementation is driven by card networks and individual financial institutions
Impact on 3D Secure Implementation
1. Standardization:
SAMA’s mandate ensures a consistent approach across all online transactions in Saudi Arabia
This standardization can lead to higher user familiarity and acceptance
2. Authentication Methods:
The focus on OTP in Saudi Arabia may limit the adoption of newer authentication methods like biometrics
However, it ensures a uniform experience for users across different banks and merchants
3. Merchant Considerations:
Merchants operating in Saudi Arabia must ensure their payment systems are fully compliant with SAMA’s 3D Secure requirements
This may require specific customizations for the Saudi market
4. International Transactions:
Saudi cards used internationally and international cards used in Saudi Arabia must still go through the 3D Secure process
This can sometimes lead to friction, especially if users are unfamiliar with the Saudi-specific implementation
SAMA’s strong stance on 3D Secure reflects the Kingdom’s commitment to securing digital payments and aligns with global trends towards enhanced online transaction security. While the specific implementation may differ from other regions, the core goal of reducing fraud and protecting consumers remains consistent.
Conclusion
3D Secure has become an indispensable component of the global e-commerce ecosystem. From its inception as a Visa innovation to its current status as a regulatory requirement in many regions, including Saudi Arabia, this technology has consistently evolved to meet the changing landscape of online fraud. The balance it strikes between robust security and user experience, coupled with the significant advantage of liability shift for merchants, has cemented its place in digital transactions worldwide.
As we look to the future, the continued evolution of 3D Secure, particularly with version 2.0, promises even greater security with reduced friction. While implementation may vary across different regions, the core principle remains the same: protecting consumers and merchants in an increasingly digital marketplace. As e-commerce continues to grow and new payment technologies emerge, 3D Secure is likely to remain at the forefront of online payment security, adapting and improving to meet new challenges in the ever-changing world of digital commerce.
Moyasar Financial Company
Under the Control and Supervision of the Saudi Central Bank.


Moyasar Financial Company
Under the Control and Supervision of the Saudi Central Bank.


Moyasar Financial Company
Under the Control and Supervision of the Saudi Central Bank.

